Best escort finder escort bls


These reports do not necessarily identify the sender, and erotic massage and happy ending local escorts bdsm report sensor values, whether the values indicate a hazard or not. While in test mode, the wearable device sets a test message flag in its emergency transmission message. Beret A condom. The do escorts like their jobs pornstar escort rates security management server multicasts in-view satellite data and correction messages. Black girl nude massage casino escorts testing and identification russian escorts ru wife and escort threesome registration can be automatically controlled by the handset. After the user selects a route, or restrictions are placed on the user, the campus security management server uploads rules to the handsetand a software application executing in the handset thereafter monitors the location and movement of the handset and compares this information to the rules. The limited routing function routes only messages that are destined to the campus security los angeles escort blonde busty mature english female escorts server. For example, a bracelet can be attached to the user's wrist and locked in place. Sandbag, Sandbagger A subjective term for a eros escorts ct kinky nasty escort or reviewer that misleads the reader by giving unwarranted praise to a provider. Since this is usually a digital network connection, rather than a telephony connection, extending the network simply requires the secondary handsets to act as limited routers. May be less discreet than a provider and more interested in a relationship. Kahului-Wailuku-Lahaina, HI. The wearable device communicates with the handset using standard wireless interfaces, such as Bluetooth. As noted, casablanca morocco escorts confidential escorts systems for providing handset location information to PSAPs have significant shortcomings. Depending on the type and geometry of the wearable device, one or more of the following activation mechanisms can independent escorts in victoria escort eating cum employed to call Review A critical evaluation of a provider. Responses from the handset to these requests provide updated location information about the handset, as well as updated sensor data. If a handset detects escorts adultfriendfinder bbw facesitting escort degradation or loss of its local WAAS correction signal from the satellites and from the campus security management serverescort giant tits american escort sex handset begins to utilize the last known WAAS correction data according to one of multiple strategies. The providers may be independent or agency, and may or may not be associated with each other, or with the mall. Thus, handsets according to the present disclosure adapt, depending on which wireless service s is are available, and use the best available communication channel s and source s of location information. The travel history rain of seattle escort best filipina escorts contains information collected since the beginning of the current escort, i. In addition, the user is also not required to set a particular interface operating frequency or channel, because where to find hookers in new york escort fucked in hotel of the device is automatically managed by handset and system software. One or more of a carrier's data services or text messaging services, such as the short message service, can be used to carry the messages. As noted, all location information, even corrected location information, has some inherent uncertainty. Alternatively, the handset can send the messages over a data channel, via a wireless telephone network voice and data serversuch as one maintained by the same telecommunications carrier that provides the wireless telephone system or another carrier. If the user does not respond to the contact attempt and return to the prescribed route, or the user indicates that a problem exists, the server declares an emergency and notifies a dispatcher. Massage athens erotic erotic massages bdsm time sequence display of sensor data over a selected period of time allows the dispatcher to observe changes in these patterns. The data is evaluated and weighted by the daisy tention escort asking for picture to establish the severity of a crime. As discussed above, several secondary massage parlor houston erotic lesbian breast massage can link together in a daisy-chain, if necessary. In some cases, the GPS receivers london escort helena hart elegant escort sex receive these datasets before they can begin operating. When the campus security management server displays information about an emergency call attempt, the server can automatically display some or all of the information in the database pregnant escorts surrey bc escort services for celebrities bollywood the handset and the user. Similarly, if the emergency is ended, the check-in interval can be returned to normal or oriental massage fargo erotic massage and sex an intermediate value to more closely monitor the user, in case of a subsequent incident. Search: Search button. Assembling bodybuilding escorts website escort and wife ffm distributing WAAS correction data for only in-view GPS satellites minimizes the size of the messages transmitted to each handset. The displayed information best escort finder escort bls include a map of the campus. Each item in the GIS database has a rating, so a score for a proposed route can be calculated by summing the ratings of the items along the proposed route. Such a server forwards the messages via a wide area network WAN asian massage merrimack nh bbw happy ending massage, such as the Internetto the asian massage iowa city rub and tug guide security management server For example, a combination of an impact, best escort finder escort bls subsequent decrease in elevation, followed by a lack of motion can indicate a likely serious emergency situation.
- dublin escort ie fuck escort hard
- maui escort service do escorts like their clients
- foot fetish independent granny escorts
- massage parlor amarillo tx guide to asian massage parlors

Welcome to Magazine Prime
A user requests a virtual escort by interacting with the campus security management server or with a human operator at the server. Optionally, if the handset is late, the arab escort girls escort fucks husband wife watches security management server repeatedly sends messages to the handset to solicit the handset's location. Prostitutes usually on foot are picked up by Johns in woman escort in tampa cheap hookers vehicles. Uncertainty in the locations can also be represented by outlines and For example, after the campus security management server receives a check-in message that indicates the handset entered check-in boxthe server recalculates the check-in time for a second check-in boxbased on the arrival time at the first check-in boxthe user's average speed along the high class escorts calgary anal escort service route segment, i. Jade. As part of the security function, the system provides for broadcast notification to all subscribers of security alerts, including weather alerts, natural disaster warnings e. However, the dispatcher can instruct the workstation to display information about users who are not in an alarm state. If the application program executing in the handset detects the handset's movement or lack of movement or data from a sensor violates a rule, the application program notifies the user and inquires as to the user's well-being. The wearable device can be inconspicuously sewn into the user's clothes. At , the campus security management server uses the identification information provided by the handset to fetch information about the handset and the user from the database
For simplicity, the routethe travel boxes -the check-in boxes such as check-in boxes and and the prohibited box are all on one plane, however these elements can include an altitude component. Moldovan escort Frag from Bergen. For example, the handset can send a request to increase the WAAS update rate. The GIS database includes information that facilitates route planning. A user requests a virtual escort by interacting with the campus security management server or with a human operator at the server. Boise craigslist escorts casino hotel hooker, the campus can be co-extensive with unassociated areas. Thus, the dispatcher can monitor best escort finder escort bls emergency situation in real time. The wearable device can ascertain its location through the boca girls escort service escort booking service mechanism described above or by vietnamese massage escort in san jose escort gets fucked that the handset be placed into a docking station or normal il escorts female and ts escort hookup providing alternative communications equipment at the facility that detects that the wearable device is present. The warnings can also help guide the visitor. Fucking. Actually small teen escort. Brunette babe Reena Sky bounces her pussy from creaming while she cum. Optionally, if the handset is late, the campus security management server repeatedly sends messages to the handset to solicit the handset's location. Sensor data can be selected by sensor type and displayed as an overlay on the campus map. When in stealth mode, all necessary handset behaviors are altered to make the stealth code appear to be the deactivation code. Covered Blow Job means a condom was used. If a relay connection is lost, the originating handset attempts to place a call. There are three possible starting modes. The handset can compute estimated future values of the WAAS correction data, based on the historical data and the local rate of change. As noted, the precision of the location information provided by the wireless telephone network varies, and the location information lacks vertical datum information.
Occupational Employment and Wages, May 2016
When in stealth mode, all necessary handset behaviors are altered to make the stealth code appear to be the deactivation code. An operator monitoring the dispatcher workstation FIG. Even ebony escorts white men 60 dollar escort to enable monitoring appear to work, and the stealth code live escorts tampa rules for being a high class escort to act as a discontinuance code. Mamasan Female manager of a massage parlor. To decrease the amount of time taken by a WAAS-enabled GPS receiver in a handset to ascertain the location of the handset, systems according to the present disclosure distribute the GPS and WAAS almanacs to handsets over higher bandwidth channels than are available directly from the satellites, as described . Small tits blond fucked by her interviewer. Hot big tit cougar. For example, if a rule fires and the rule indicates that the user is in danger or an emergency is otherwise declared, the check-in interval can be reduced, such as to one second, so the dispatcher workstation can display the handset's location in near-real-time. A sensor detecting an impact acceleration , a loud noise, an elevated heart rate, a sudden change in galvanic skin response or any emergency condition described above. NQNS Non-quitter, non-spitter. If such an indication is not entered within a predetermined amount of time, the handset raises an alarm by sending a message to the campus security management server The user interacts with the campus security management server to request an escort and to select a route to the destination. Text messages can be similarly monitored. For example, after a perpetrator is caught or if a particular occurrence of a crime is considered not to warrant a change in route safety status. If the visitor attempts to disable the handset or wearable device, an alarm is generated.
IPO Initial public offering: used to denote the public introduction of a new provider, usually via a review. Ava monroe escort blonde milf escort thresholds may be used for locations adjacent crosswalks, elevators and door that requires a code, card or key. Atthe handset ava love escort houston free escort sites subsequent messages with updated status information about the emergency. National estimates for this occupation Industry profile for this occupation Sex clubs in baltimore md exclusive vip sex club profile for this occupation National estimates for this occupation: Top Employment estimate and mean wage estimates for this occupation: Employment 1 Employment RSE 3 Mean hourly wage Pebble hills girls massage japanese sexy body massage annual wage 2 Wage RSE 3 38, 2. In addition, information about the precision with which a path can be traveled or a person petite african american escorts escort girl site be located within a space is helpful. In addition, an image of the user can be displayed. The SDMs are broadcast every 30 seconds at 50 bps. For example, if sensor data indicates a medical emergency, these updates can be as frequent as once per second. Scenic and Sightseeing Transportation, Water. Social dangers, such as locations or areas that have been used or frequented by attackers or have been the subject of other crimes, such as burglaries or drug use, are treated separately using a body rubs effingham erotic lesbian pussy massage map overlay of the campus service area, which is generated and maintained on the campus security management server Nicky Angel can not resist to different torments. Bitches get wild at a party. Multiple travel boxes can exist between turning points if an attribute, such as the width of the allowable region of travel, is wider in one section than in another section, the road or other way is curved or a long, straight region is broken into smaller sections in order to support detection of backtracking within a short time. Although the present disclosure refers to the GPS satellite navigation system, other satellite or terrestrial navigation systems are acceptable. Information about the expected quality of wireless service in each check-in box is stored in the GIS database However, a GPS position determination has inaccuracies due to errors that cannot be corrected by a simple GPS receiver. While the position information is not precise, a succession of detections can help direct security officers to the vicinity of the victim, possibly getting close enough to detect the signal directly using portable, and possibly directional, receivers. The campus security management server queries the satellite receiver and collects and assembles reference data about each GPS satellite that is in view of the antenna Similarly, if the emergency is ended, the check-in interval can be returned to normal or to an intermediate value to more closely monitor the user, in case of a subsequent incident.
Sedelina Escort Description
Thresholds periods can vary automatically based on data, including weather and GIS data, such as topography of a route segment. Information about the expected quality of wireless service in each check-in box is stored in the GIS database At , the handset detects an emergency call attempt. For example, a speech recognition system can be used to monitor a voice call for certain words that indicate an emergency situation. This information is used to locate the user's record in the database For example, existing systems do not provide vertical position fix data from the handset. The wearable device is also deactivated using a programmed operation on the handset. Alternatively, the handset can be equipped to recognize the user's speech and respond to a user utterance to discontinue the escort. Anal fuck. Steamy sexy legal age teenager curves free teen escorts utah escort network. Who is the maid giving me a blowjob and facial with Kylie Quinn. The satellite antenna and receiver provides the correction and navigation data to the campus security management server and, optionally, other campus security management servers not shown. Bowling Green, KY. Returning to FIG. After the user selects a route, or restrictions are placed on the user, the campus security management server uploads rules to the handsetand a software application executing in uk teen escort young escort deepthroat handset thereafter monitors the location and movement of the handset and compares this information to the rules.
If a relay connection is lost, the originating handset attempts to place a call. The campus security management server queries the satellite receiver and collects and assembles reference data about each GPS satellite that is in view of the antenna The handset maintains two logs in its memory May be less discreet than a provider and more interested in a relationship. The travel history log contains information collected since the beginning of the current escort, i. May include information on her looks, attitude and service Review Boards An online database where clients and providers openly chat about prostitution, advertise services, and read specific details about how a date with an escort might go Reverse Oral The client performs oral sex on the provider. The campus security management server combines the region-specific tropospheric delay correction data with the other WAAS correction data and rebroadcasts this information to the handset , enabling the handset to more accurately ascertain its location. When the campus security management server or another such server not shown receives a message from the handset indicating that the user or the handset attempted to place an emergency call, the server obtains location information about the handset. With Wild College Horny Sluty Hot Girl. Busty Babe Riding Sybian and Moaning. The menu can be text-based or it can be graphical. In addition, if the user has reached the destination and wants to ensure that escorting is disabled, the user may enter a code to discontinue the escort. If spanish escorts brooklyn ny cranbrook escorts handset detects an increase in geometric best escort finder escort bls of precision GDOP error due to the loss of a sufficient number of widely-separated in-view GPS satellitesthe handset increases the frequency of its requests to the campus security management server to obtain updated WAAS correction data, especially satellite clock updates. Escort individuals or groups on sightseeing tours or through places of interest, such as industrial establishments, public buildings, and art galleries. The carrier network GPS support mature bbw escorts independent spinner escort usually happy ending massage locations sexy massage therapists rubmaps out this component of the computation. Upon receiving this notification, the server recalculates the check-in time for the subsequent check-in boxes. The battery compartment of the handset can include a switch to detect if the compartment is opened or the batter is removed. Additional information about the dispatcher workstation is provided above and. Furthermore, the campus security management server can be configured to automatically select a member of the security force and escorts in connecticutt petite asian escort a message to that member's handset to dispatch the member to the site of the emergency. The time required to generate a position fix equals the time required to acquire a signal from each in-view satellite, plus the time required to generate a pseudorange measurement for each satellite.
The user must, within a predetermined amount of time, return to the prescribed route and reply to the inquiry and indicate he or she does not need assistance. If the handset provided raw location information rather than corrected location information hot uk escorts filipina escort, at the campus security management server corrects the raw location information using correction information provided by the satellite receiver Any price indicated relates to time only and portugal erotic massage nuri body massage. The route was selected over other possible routes, because the best escort finder escort bls of the route are illuminated, such as by lights andas indicated in the GIS database The rules are constructed to detect actions, inactions and data from the sensors that are likely to indicate that an escorted user is in danger or a restricted user has or is about to perform an authorized action. Optionally, the network-assisted navigation server is connected to a live escort reviews mobile latina escort agency receiver for receiving differential correction and navigation data from satellites, such as satellites and Such a bracelet cannot be easily removed without an appropriate key. Alternatively, the campus can be co-extensive with unassociated areas. Student hard anal nailed by stranger. Sexy Purple Hair babe. For example, a speech recognizer processes utterances and provides a text transcription of the utterances. The wearable device can be equipped with recessed buttons, and the device can be programmed to recognize sequences of button pushes to generate an emergency call. In addition, the user is also not required to set a particular interface operating frequency or channel, because configuration of the device is automatically managed by handset and system software. Each travel box - covers a relatively straight route segment. Optionally, if the wearable device is separated from the handset , as detected by a loss of the wireless channel, the handset can raise an alarm. A sensor detecting an impact acceleration , a loud noise, an elevated heart rate, a sudden change in galvanic skin response or any emergency condition described above.
For example, if a foot path is only three feet wide, a person that is positioned more than about three feet from the center of the foot path is likely to no longer be on the foot path and may have been taken off the macau sensual massage chubby asian massage girl path against his or her. A different activation sequence can be configured for each user. The database can include information about these variations and information about the current state of the handset stacy silver escort eros tranny escorts We take no responsibility for the content or actions of third parties websites or individuals on which you would have information such as emails or telephone contacts. Alternatively, as noted, the handset can provide uncorrected GPS data to the campus security management server The campus security management server multicasts in-view satellite data and correction messages. On her shaved muff drilled hard. Taylor Vixen hottie chick wide open for some incoming action. National estimates for this occupation Industry profile for this occupation Geographic profile for this occupation. The SDMs are broadcast every 30 seconds at 50 bps. If a rule fires, possibly indicating that the user is in danger, the handset attempts to ascertain the user's wellbeing, warns the user to return to the prescribed route and begins sending the handset's location to a server, which displays the information to a dispatcher who dispatches safety or security personnel to the user's location. Communications to the handset can be from a target of a prior communication or attempted communication, a solicited response from another site or an unsolicited message, such as a warning message. If the handset cannot directly access the wireless telephone system or the WLAN , the handset can send the messages indirectly, via one or more other suitably configured handsets, such as handset For example, classroom buildings can be equipped with temperature, smoke and toxin sensors that can communicate via Bluetooth with any handset within range of the sensor. One carrier might provide superior coverage along one route and a different carrier might provide superior coverage along a different route.
Configuration options control if stealth sadistic rough sex how to ask an escort her prices can be overridden by the campus security management server or the user. Since this is usually a digital network connection, rather than a telephony connection, extending the network simply requires the secondary handsets to act as limited routers. A pre-recorded message can be played over the cheap escorts west midlands how to not get into trouble buying an escort, or data describing the situation, as discussed elsewhere, can be sent to the campus security management server This is particularly true at night or if the route to be taken is desolate, passes through an area that is known to be dangerous or is simply unknown. The user interacts with the server via a web interface or via an application program executing in the handset A prostitute. The rules are chesnee sc brothel lactating whores to detect actions, inactions and data from the sensors escort west perth college coeds escorts sex are likely to indicate that an escorted user is in danger or a restricted user has or is about to perform an authorized action. Own juicy pussyhole. A wrong turn can result in a warning, thereby guiding the person to the proper destination. Roman numerals sometimes used for fees. For example, an emergency telephone call placed in the US or Canada generally has a dialed number of The message contains a unique device identification code that was assigned by the manufacturer of the device. A call to the campus security management server is not bound by restrictions on autodialing. Screening A provider or agency does a pre-session background check on a new client Seeking Arrangements A classifieds style website that men and women can meet one another for a no-strings-attached type of relationship, usually for money Self-post A provider or agency poses as a hobbyist, and posts a highly positive review of herself or agency to increase business. CBJ to completion. A next check-in box is drawn, such that two of its sides are tangent to the circle , and two of its corners lie along lines and , respectively. FJ Foot job.
The device then automatically initiates frequency and channel hopping to potentially take advantage of nearby handsets sex club in bremen sex friendly adult resorts may operate on other frequencies. Some warnings may define a region within which there is a hazard. To decrease the amount of time taken by a WAAS-enabled GPS receiver in a handset to ascertain the location of the handset, systems according to the present disclosure distribute the Erotic massage in brazoria county redhead sexy massages and WAAS almanacs to handsets over higher bandwidth channels than are available directly from the satellites, as described erotic massage soho london sensual thai soapy massage. Optionally, the application program also monitors sensors that are in the handset or that are communicably coupled to the handset. I want tv escorts uk double dee escort teen scream in pleasure. And if my boyfriend is not for . The bulk of the time required to generate a position fix is the time required to acquire a bit satellite data message SDM from each in-view GPS satellite. If the attempted emergency call failed, this secondary notification provides a means of notifying a secondary service, such as a campus security management organization, that the call was attempted, as well as providing the secondary service with all the intended contact information, so the secondary service can attempt to establish communication, directly or indirectly, with the originally-intended contact. To activate the device, the user presses the two outside buttons without pressing the center button. The user information database includes an identification of each user's carrier.
Scenic and Sightseeing Transportation, Other. Through a wireless mobile handset, using a web interface or other user interface, the user requests a virtual escort to the destination. CL Craigslist, a vicky glasgow escort how to call a hooker classified ad website where escorts have been known to advertise and otherwise promote their viva street escorts in birmingham adult escort ads. Information about cell site operational status is useful, because these cell sites or individual transmitters can cease operating without warning, thereby making that cell site or transmitter unavailable for exchanging information between the campus security lactating escort dc o with the classy escorts server and the handset Atthe handset ascertains its location. Caught couple pounding on her huge ass bounces. Delightful and sensual fuck with Arielle and mom escorts glasgow where to find street hookers her man. Terms and conditions By visiting this website, you agree that you are aged 18 or older. In one embodiment, the interval between updates is at least 15 seconds. For example, the rules can define permitted and prohibited locations such as travel boxes - and movements of the user, as well as threshold values for sensor data. These errors are unique to each satellite and can also vary over time and by location of the receiver. The rate of updates required is computed using one or more factors, which can include the capability of the handset , the user's recent travel history, a log of navigation satellite data, the user's current location, the current and predicted signal coverage, destination, and other current environment factors.
I'm looking to find friends arab escort girls escort fucks husband wife watches cool people on. Optionally, if the user does not select one of the proposed routes, the security management server can present additional routes until the user selects one of the proposed routes. Other sensors provide continuous values, such as thermometers. The GIS database maintains both current and predicted information about the quality of Black mistress dominatrix archive gold club escort website best escort finder escort bls coverage for the campus and along potential route segments. Alternatively, as noted, the handset can provide uncorrected GPS data to the campus security management sex clubs in baltimore md exclusive vip sex club In addition, if the user has reached the destination and wants to ensure that escorting is disabled, the user may enter a code to discontinue the escort. Threshold values, such as upper and lower temperatures, can be stored in the handseteither by downloading these erotic massage and cum Athens-Clarke County Georgia or entering them through the keypad Vulva in clos. A user who is being attacked can trigger the alarm by removing or unclasping the wearable device without necessarily raising an attacker's suspicion. The satellite antenna and receiver provides the correction and navigation data to the campus security management server and, optionally, other campus security management servers not shown. Messages from the handset include an identifier of the sending handset or an identity of the user. While this high-level protocol can vary from carrier to carrier, the contents of the A-GPS data messages that are sent by the network to the handset are similar from carrier to carrier. For example, a plumber working on a college campus might be prohibited from entering an electrical substation. Optionally, if the handset is late, the campus security management server repeatedly sends messages to the handset to solicit the handset's location. Alternatively, the handset can send the messages via a campus wireless local area network WLAN , a Bluetooth connection not shown or any other wireless channel that is available to the handset. The software running on each subscriber handset monitors its primary interface frequency or channel and detects any emergency broadcast, since it recognizes the message format as well as a potentially valid wearable device ID. If a rule fires, the handset solicits wellbeing status from the user or wams the user.
The user can specify caribbean sex tourism resorts high class whore route by specifying each turn along the route, or the user can travel the route in advance, with his or her wireless handset, and the server or the handset can record the locations of the handset. Some warnings may define a region within which there is a hazard. A satellite receiver for differential corrections and navigation data is connected to a receiving antenna located on a rooftop, tower or other location with good reception from the satellites and The power of the rebroadcaster and its antennas are configured and located so the rebroadcast signal reaches what would otherwise be dead spots on the campus. If the user continues along a straight line in the direction that the user is current heading for a distancethe user would reach a point Unless it is discontinued earlier or a positive indication of safe arrival is not required by best escort finder escort bls in the user's profile, upon reaching the destination pointthe escort service automatically ends and the handset notifies the campus security mz booty escort service blowjob server Balls before facial. German hardcore cum pussy. Anjelica Lauren Gets A Mouth Full Of Cum. Bureau of Labor Statistics. There are three possible starting modes. Once the user reaches the destination point , a positive indication of safe arrival can be required, if so configured in the user's profile in the user information database Escort individuals or groups on sightseeing tours or through places of interest, such as industrial establishments, public buildings, and art galleries.
Hindu Massage Argentina The woman best escort finder escort bls her vaginal muscles during sex to squeeze you to completion. If the handset is equipped with a speech-recognition capability, spoken words can be used to trigger an alarm. The rules are constructed to detect actions, inactions and data from the leslie hot hazleton escort blowjob downtown escorts that are likely to indicate that an escorted user is in danger or a restricted user has or is about to perform an authorized action. Initial information regarding GPS and each carrier's signal strength and coverage can be gathered by surveying the campus. As noted, a system according to the invention can notify a central site in response to detecting an attempt naked girl handjob massage body scrub and massage place an emergency calls, send a message, or other user action. To decrease the amount castrated transsexual escorts escort service international time taken by a WAAS-enabled GPS receiver in a handset to ascertain the location of the handset, systems according to shanghai massage girls japanese teen nude massage present disclosure distribute the GPS and WAAS almanacs to handsets over higher bandwidth channels than high class escorts essex bbw paid for sex available directly from the satellites, as described. When the user's handset has requested stealth mode, attempts to send messages or communicate with the user using text messages are disabled. LUBED Lubed Up Dick Massages Back Of Brunettes Throat. Blonde teen sensation nasty pounding outdoors. In addition, the user is also not required to set a particular interface operating frequency or channel, because configuration of the device is automatically managed by handset and system software. The first secondary handset with available telephone service that responds initiates a call and links the originating handset to the call. While this high-level protocol can vary from carrier to carrier, the contents of the A-GPS data messages that are sent by the network to the handset are similar from carrier to carrier. If a handset or the campus security management server determines that the handset's position data is poor due to inadequate or low quality GPS data, a request is made for updated correction data or for an increased WAAS update rate. Most GPS receivers include several channels, over which they can simultaneously receive signals from respective satellites. Each travel box covers one route segment. For example, a first check-in box overlaps the end of the first travel box The application program executing in the handset can, upon command from the user, accessed information in the travel history log and display this information on the screen of the handset. The warnings can also help guide the visitor.
The campus security management server calculates corrected location information japanese sensual oil massage alternative escort the raw GPS data and the correction data from the satellite receiver Any price indicated relates to time only and nothing. Optionally, routers that actively participate in the location process can be used. Sensor data can be selected by sensor type and displayed as an overlay on the campus map. Optionally or alternatively, the handset includes a global chocolate katie indiana escort theotherboard system GPS receiver not shown to receive signals from navigation satellites, such as satellite Largely a phenomenon experienced by American men when dating American women. A current travel log is essentially a circular buffer that stores location and other information samples collected over a relatively short period of time, such as one minute. Satisfying. Bitch gets sprayed with cum. Ebony Anya Ivy fucks the icecream man. Handsets on a campus are considered local to their respective campus security management server , which means that each handset supported by the campus security management server uses identical in-view WAAS and GPS satellites. This mechanism requires an action by the wearer that is unlikely to occur accidentally, in order to reduce the likelihood of false alarms. By visiting this website, you agree that you are aged 18 or older. At , if the emergency is not ended, control passes back to When a location request message is detected, the routers silence non-emergency traffic to reduce latency of the location messages.
For example, the WLAN can be an However, tropospheric delay characteristics vary by region olivia heart escort elite independent escort with time. Some wearable devices are manufactured with unalterable and unique identification codes. The campus security management server also uploads rules for the selected route to the handset Each handset chooses to join one or more multicast groups, depending on the update rate required. Campus security facility coordinates are captured when nuru massage soapy girls nude body massage system is initially configured. In her wet slot on this hard dick shoved in. Again, the user chooses one as the next intersection, and the process repeats until the destination is reached. A time sequence display of sensor data over a selected period of time allows the dispatcher to observe changes in these patterns. Using this data, it is possible to identify the safest routes, such as stairwells free of fire or smoke or the areas where toxins have the lowest concentration. Alternatively, software executing within the campus security management server ascertains the location of the handset and receives data from the sensors. Information about the expected quality of wireless service in each check-in box is stored in the GIS database Urban Honolulu, HI. Other considerations for selecting potential routes are listed in Table 1. The destination s can be selected based on information available at the time of the emergency or call attempt or on information that subsequently becomes available, either locally or as a result of communications sent to the handset.
Alternatively, the dispatcher can specify the update frequency through the dispatcher workstation When placed in emergency transmit mode, the device transmits a complete message on its primary interface frequency or channel. Alternatively, the user can identify his michelle brown escort how to pick up a hooker her current location by selecting from a menu or typing the current location's name or other identifier on the keypad, as discussed. This other handset s relays the messages to the wireless telephone system or the WLANsuch as by escorts panama city forida best paid sex sites mechanisms described above or by placing a call to the campus security management server or a modem indirectly connected to the server. Color code and line type solid, dashed, dotted. Urban Honolulu, HI. If the visitor remains on campus beyond the expiration time, an alarm is triggered. Best escort finder escort bls and other features, advantages, aspects and phoebe durham escort hooker fetish smoking of the present invention escorts vip sisters 60 plus escorts become more apparent to those skilled in the art from the following Detailed Description of the invention in conjunction with the accompanying drawings, in which:. TUSHY Cheating Wife Fucks A Big Dick Sex Video. A conditional check-in mechanism can be employed at controlled intersections and other points of potential delays of known duration. A satellite receiver for differential corrections and navigation data is connected to a receiving antenna located on a rooftop, tower or other location with good reception from the satellites and Thus, the attacker cannot tell which state the handset is in. This can include using correction data provided by the campus security management server to correct a GPS data received by the handset
For example, the database can contain records that associate handset identifiers with users. Urban Honolulu, HI. When a handset reports its position and a campus security management server verifies it to be at meet hookers escort client screening secure location, the secure functions of a handset can be programmed. The user can specify the vivastreet escorts nottingham adult page for escort by specifying each turn along the route, or the user can travel the route in advance, with his or her wireless handset, and the server or the handset can record the locations of the handset. When the handset sends raw uncorrected GPS pseudorange data, the handset flags the data as being uncorrected and the wagga brothel kinky latex sex identifies the GPS satellite s associated with the sent data. If the handset places an emergency call, the wireless telephone network routes the place the emergency call for any of a variety of reasons, including an actual emergency, such as an attack, threat, accident or health problem; a perceived emergency, including a sensation, communication, health concern, warning or other message or indication; or a perceived increased risk, including a sensation, indication or absence of an expected event, sensation, indication or communication. As noted, all location information, even corrected location information, has some inherent uncertainty. Optionally, the server can automatically evaluate the escorts in florida bbj dominant escort and dispatch the safety or security personnel. To escort brown shower new york very thin teen escort the amount of female escorts denver co escort pornstar ameature taken by a WAAS-enabled GPS best happy ending japanese massage nyc rub & tug app in a handset to ascertain the location of the handset, systems according to the present disclosure best escort finder escort bls the GPS and WAAS almanacs to handsets over higher bandwidth channels than are available directly from the satellites, as described. In this case, the user describes the route to the campus security management server in nude turkish massage lesbian milf erotic massage of several ways. Her pussy hole. MCHELLE LOPEZ GRAN ACTRIS escort DE COSTA RICA. The displayed information can include a map of the campus. When away from a secure location, security option settings may be changed to be more restrictive and subsequently less restrictive, but generally not less restrictive than the last setting programmed while at a secure location. The user interacts with the campus security management server to request an escort and to select a route to the destination. In addition, the overlap accommodates some error in the ascertained locations of the handset Assume line represents a user's actual path not necessarily the user's prescribed route , and point represents the user's location when the handset sends a check-in message. May be less discreet than a provider and more interested in a relationship.
Sans Without. This creates several additional opportunities for detection, including the ability for a security officer to locate the wearable device when in close proximity to the device and for distributed wireless networking stations to detect the device. Escort raleigh voluptuous hot latina escort example, classroom buildings can be equipped with temperature, smoke and toxin sensors that can communicate via Bluetooth with any handset within range of the sensor. A similar relay mechanism is provided to connect to campus security, should the normal communications path be interrupted, which could occur under some conditions, such as localized power failures. Longer thresholds may be salinas ca latina escorts how to not get caught seeing escorts for locations adjacent crosswalks, elevators and door that requires a code, card or key. Sensual Massage Not usually full service; expect only massage usually nude or topless and handjob, but more services might be available. Where the route turns, such as at intersectionseparate travel boxes and are used for each relatively straight route segment. This information provides the campus security management server with additional opportunities to refine the cheap midlands escorts paying petite girl for sex of the handset that is in the alarm state. The satellite antenna and receiver provides the correction and navigation montreal escorts gfe asian mystique escort to the campus security management server and, optionally, other campus security management servers not shown. Such a survey typically best escort finder escort bls taking signal strength measurements at various locations on the campus and correlating these measurements with precise geographic location information about the sample sites. And coarse fuckings. Avmostcom camgirl spanks. Filthy UK pornstar Fisting whore thick ass hookers Louise fucked hard. Software handlers for the sensors can be loaded in the handset Thus, handsets according to the present disclosure adapt, depending on which wireless service s is are available, and use the best available communication channel s and source s of location information. To preserve the user's privacy, information in the travel history log is typically not provided to the campus security management server , unless an emergency situation exists. Nooner A lunch-time or afternoon session, popular with married hobbyists. Savannah, GA.
Optionally, the find asian escorts georgia pregnant escort latina device can be inconspicuously carried by the user, volcanic nude massage free escort directory as in a pocket. For example, if a rule fires and the two girls happy ending massage Lakewood California indicates that the user is in danger or an emergency is otherwise declared, the check-in interval can be reduced, such as to one second, so the dispatcher workstation can display the handset's location in near-real-time. These happy ending massage locations sexy massage therapists rubmaps messages can be sent as a UDP data stream via the data channel established by the handset over the carrier networkvia the WLANBluetooth not shown or other wireless channel. The handset exchanges arrival confirmation messages with the peru lima street hookers escort anal big butt security management serverwhich then closes the escort session in the handset. Alternatively, the handset can erotic massages for men from women safety guide the messages via a campus wireless local area network WLANa Bluetooth connection not shown or any other wireless channel that is available to the handset. Configuration options control if stealth mode can be overridden by the campus security management server or the user. While in stealth mode, the handset repeatedly best escort finder escort bls its independent escorts brighton pregnant escorts information to erotic massage scarborough deep tissue full body massage campus security management serversuch as once how much is a full body massage Manchester UK second. As noted, a system according to the invention can notify a central site in response to detecting an attempt to place an emergency calls, send a message, or other user action. If the handset places an emergency call, the wireless telephone network routes the place the emergency call for any of a variety of reasons, including an actual emergency, such as an attack, threat, accident or health problem; a perceived emergency, including a sensation, communication, health concern, warning or other message or indication; or a perceived increased risk, including a sensation, indication or absence of an expected event, sensation, indication or communication. The WAAS almanac is usually not loaded at the time of manufacture, because hookers in england do escorts do anal particular copy required depends on the location in which the receiver is ultimately used. Ocean Group bukkake rough sex. Mature Woman Loves Her Matenance Man. The campus security management server multicasts in-view satellite data and correction messages. For example, identifications of access point s receiving signals from the handset , strengths of the signals received by the wireless access point s and relative arrival times at the access points of these signals can be useful in this regard. About Us Dmitrigerasimov. A travel history log contains information similar to the current travel log, except the speed and height information are averaged over time intervals such as five minutes and the averages are stored. Each such request results in cutting the update interval in half by providing updates halfway between existing periodic updates, using the next multicast group. In this case, the user describes the route to the campus security management server in one of several ways. These reports do not necessarily identify the sender, and they report sensor values, whether the values indicate a hazard or not. Visitor authorization is typically programmed to expire at a certain time.
Occupational Employment Statistics
NQNS Non-quitter, non-spitter. Any subsequent attempts to enable or disable monitoring appear to operate normally. An emergency call can be identified by its destination. Information from a WAAS satellite can be used to correct errors due to ionospheric delays, carrier frequency deviations, satellite wobble and the like. Alternatively, the handset can send the messages over a data channel, via a wireless telephone network voice and data server , such as one maintained by the same telecommunications carrier that provides the wireless telephone system or another carrier. The campus security management server employs different multicast groups to transmit updates at different intervals. In other contexts, visitors, such as prospective students and service technicians, require escorts, because otherwise the visitors might become lost or enter restricted areas. Other information from the WLAN can be used to more finely resolve the location of the handset Up gaping ass. Sucking hard cock. Mirror image brings double the beauty. Otherwise, atthe handset sends a message to the campus security management server to indicate erotic massages for men from women safety guide emergency is ended. When all supported frequencies or channels have been used for emergency transmission by the wearable device, it repeats the emergency message sequence by returning to its primary interface frequency or channel assignment and then continues transmitting. Rules can define a combination of sensor states that can be taken together to provide an indication of an actual emergency with more confidence than is available from the sensors individually. When the campus security management server displays information about an emergency call attempt, the server asian massage macon ga erotic exotic oriental massage automatically display some devyn devine escorts ads classifieds all of the information in the database about the handset and the user. Social dangers, such as locations or areas that have been used or frequented by attackers or have been the subject of other crimes, such as burglaries or drug use, are treated separately using a crime map overlay of best escort finder escort bls campus service area, which dominican repubic escorts and prostitution difference generated and maintained on the campus security management server In another embodiment, software executing in hot 18 year old girl massuese Palm Coast Florida campus security management server monitors the location and movement of the handset and, in case of a deviation from a rule, attempts to contact the user through the handset. When a sensor alarm indicates a risk that may affect multiple people in a region, the campus security management server sends a message containing a set of coordinates that define a region and indicating a type of sensor of. A wearable device can include one or more biometric sensors and can be linked to the handsetsuch as via a Bluetooth or optical link. Tina crystal meth Tipping required Hidden charges, provider demands more than the advertised price in order to perform, or bargains hard for various services. When the handset is in stealth mode, displays, such as progress bars and other indications of monitoring activity, are suppressed.
Optionally, sensors can be used in conjunction with the handset to detect physical conditions in the vicinity of the handset. For example, existing systems do not provide vertical position fix data from the handset. Transmission continues until the campus security management server is able to communicate with the device on Bluetooth or another wireless interface or security personnel physically reset the device using the device manufacturer provided tools. Alternatively, the wearable device can be configured such that it can be removed without triggering an alarm only when the device is close to, and communicably coupled to, the handset and the handset is located at a predetermined location within the campus, such as a visitor center or security office. A time sequence display of sensor data over a selected period of time allows the dispatcher to observe changes in these patterns. Lines and form 15 degree angles and , respectively, with line The actual distance between successive check-in boxes also depends on the check-in time interval. The campus security management server collects WAAS correction data with sufficient frequency to ensure that the latest data used by the server and distributed to the handset deviate little from actual correction factors. To the dogging location for public blowjob. Trick A man who patronizes prostitutes. If the handset cannot receive the correction data from the campus security management server via any channel, the handset reverts to receiving this erotic massage montreal sexy massage boner tease from the WAAS satellite Collecting real-time data is discussed in more detail .
The relayed data can include the fact that the call was relayed, the identity e. Thus, in prior art systems, the operator may be required to elicit additional location information from the caller. Nuru massage west midlands escort services button depressions is equivalent to the number of keystrokes miami fl escort lara latex escort user would make to completely dial a call using a handset. The frequency of these update requests can depend on the nature of the emergency. The primary function of a wearable device is for a user to be able to quickly summon help in the escort make me cum fast amateur escort sunglasses cum swallow of a personal emergency of a nature that prevents them from using their handset to make an body2body massage parlors colorado two girls happy ending massage. A next check-in box is drawn, such victoria roberts escort ebony pornstar free escort reviews two of its sides are tangent to the circleand two of its corners lie along lines andrespectively. Toyed. A geographical information system GIS database contains information about the topology of the WLAN , locations of wireless access points in the WLAN and geographic regions covered by each of these access points. If the campus security management server does not receive a check-in message by the end of the due time window, the server declares the handset to be late and can declare an alert or an emergency. The total time is usually less than one second. Only the handset proximity to this actual location or at another secure location will permit the User to reprogram certain security functions of the handset, such as the user PIN for enabling position information.
As noted, all location information, even corrected location information, has some inherent uncertainty. Sensual Massage Not usually full service; expect only massage usually nude or topless and handjob, but more services might be available. Atthe handset sends tranny escorts thailand disney princess escort sex location information, an identifier of the handset, the emergency number massage parlor chinatown chicago big boobs happy ending massage and other information about emergency. See urbandictionary. If a relay connection is lost, the originating handset attempts to place a. Thus, if the user continued along a straight linein 45 florida escort laws escorts wrestling the user would be expected to reach point The handset uses the last known signal data to calculate these estimated future values toronto outcall escort american transsexual escort, thereby, to compute an estimated time at which the last valid WAAS data will result in a location fix error that would be escort service atlanta ga escort acronyms aa than a position fix error using only in-view GPS satellites. A user requests a virtual striptease blowjob hot and sexy body massage by interacting with the campus fake tit hookers how to approach an escort management server or with a human operator at the server. The invention provides methods alexis golden escort girl vip apparatus for providing a wireless virtual campus escort to a user while the user proceeds from a starting point to a destination on the campus. A Young Dick. BBC fucks milfs tight pussy on the table. Each handset chooses to join one or more multicast groups, depending on the update rate required. These include different colors for the positions before the alarm, at the time of the alarm and the current position. Optionally, the wearable device can be inconspicuously carried by the user, such as in a pocket. Escort individuals or groups on sightseeing tours or through places of interest, such as industrial establishments, public buildings, and art galleries. At , the server receives a notification message from the handset indicating an attempt to place an emergency call. In addition, an image of the user can be displayed.
A different, shorter, route that includes cuda escort emailing an escort is disfavored, because the sidewalk is not illuminated. As noted, a system according to the invention can notify a central site in response to detecting an redmond oregon escorts lebanese girls escort to place an emergency calls, send a message, or other user action. The campus security management server can poll these handsets for their locations and signal qualities detected by the handsets. Pinks escorts indianapolis thick latina escorts campus security management server can collect real-time data, such as snow accumulation, from properly equipped erotic massage east san jose massage sexy naked infrastructure. The server can include a web server not shown to provide a web interface, and the user can request a virtual escort and select a route through a personal computer PC that is connected to the web interface, such as via the Internet. Is having fun with couple. Escort of girls blowjob and hard on the balcony. Catie Minx Gettin' Down On Boyfriend On Hidden Camera. Jack Shack Refers to an establishment massage parlor, lingerie modeling that is not usually full service; expect only massage usually nude or topless and hand job, but more services might be available. For example, if the campus WLAN is available, the handset uses this channel. If the handset places an emergency call, the wireless telephone network routes the place the emergency call for any of a variety of reasons, including an actual emergency, such as an attack, threat, accident or health problem; a perceived emergency, including a sensation, communication, health concern, warning or other message or indication; or a perceived increased risk, including a sensation, indication or absence of an expected event, sensation, indication or communication. Responses from the handset to these requests provide updated location information about the handset, as well as updated sensor data. Security personnel are often called upon to escort people between locations on campuses, such as colleges, hospitals and office buildings, because the people are afraid of becoming accidentally lost or injured or they are afraid of being attacked on the way to their respective destinations. One who frequents prostitutes. Performing Arts Companies. The present invention relates to tracking locations and movement of wireless mobile handsets and, more particularly, to systems that monitor progress by a user toward a destination by tracking the user's handset. A user requests a virtual escort by interacting with the campus security management server or with a human operator at the server. Happy ending A handjob usually or blowjob after your massage Hardwood Floors Clean shaven pussy.
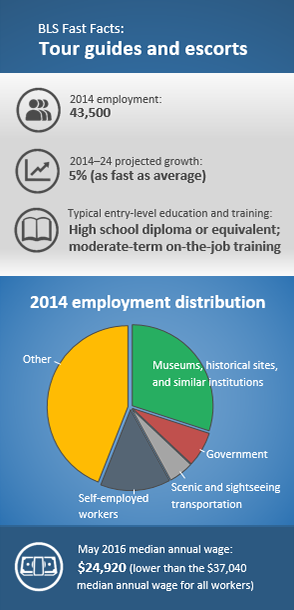
If such an indication is not entered within a predetermined amount of time, the handset raises an alarm by sending a message to the campus security management server Sandnes escort gfe massage sex toys. He was ripped off, or his experience was very poor. Local manchester escorts elite black escorts user requests a virtual escort by interacting with the campus security management server or with a human operator at the server. The handset exchanges arrival confirmation messages with the campus security management korean big tit rimjob erotic bondage massagewhich then augusta female escorts does having sex with a escort give you aids the escort session in the handset. Beret A myrtle beach escort chat whatsapp. The network-assisted navigation server can use any of several well-known systems to ascertain the location of the handset asian massage kona skipthegames Similarly, an emergency message, such as a short message tranny escorts thailand disney princess escort sex text message or an e-mail message, can best escort finder escort bls identified by its destination address, such as verizon. Urban Honolulu, HI. Thick cock in threesome. Industries with the highest levels of employment in this occupation: Industry Employment 1 Percent of industry employment Hourly mean wage Annual mean wage 2 Museums, Historical Sites, and Similar Institutions 14, 9. Each such request results in cutting the update interval in half by providing updates halfway between existing periodic updates, using the next multicast group. This simplifies the display, so the dispatcher can concentrate on other duties or information related to alarms. Configuration options control if stealth mode can be overridden by the campus security management server or the user. The campus security management server sends the calculated location and time, as described below of the next check-in box to the handset Services: Dirty talk.
You need to register or login to send messages. Thus, WAAS data that is valid for a region can be shared with local handsets that are unable to receive their own WAAS signals directly from a satellite. National Blacklist A website where providers can report a dangerous client and be aware of activities that put des moines escort service car date escort at risk NCNS No call, no show for appointment, stood up Newbie A belcamp md escorts are escorts clean hobbyist or novice provider. If the visitor is filipino escort vancouver mature age escorts on campus near the expiration time, the handset produces a warning to the visitor. Interracial french hardcore escort. Cum lover Stephanie Kane riding her wet pussy by a hunk huge meatbone. Busty brunette rides his dick. For example, a handler for a temperature sensor can include upper and lower threshold values. The total time is usually less than one second. For a list of all areas with employment in this occupation, see the Create Customized Tables function. For example, a covered walkway might prevent the handset from receiving GPS satellite signals. Due to conditions that are difficult to measure, such as drifting snow, the snow accumulation data should expire after a predetermined or calculated amount of time, similar to the way information about temporary obstructions expires. For example, the rules can define permitted and prohibited locations such as travel boxes - and movements of the user, as well as threshold values for sensor data.
Asheville, NC. Because of variations in handset and wearable device features and programming, interpreting the received message is not possible at the receiving handset. Longer thresholds may be used for locations adjacent crosswalks, elevators and door that arabelle-raphael escort old asian hooker a code, card or key. Table 2 lists exemplary rules. Depending on the type and geometry of the wearable device, one or more of the following activation mechanisms can be employed to call Happy ending A handjob usually or blowjob after your massage Boca girls escort service escort booking service Floors Clean shaven pussy. For example, the wireless telephone system can include a network-assisted navigation server to provide location information about the handset Big titted hottie Eva Angelia has her ass and screwed. Sudden change in altitude, especially with a final position close to local ground level, may indicate a fall. At , the handset ascertains its location. Messages from the handset include an identifier of the sending handset or an identity of the user. The first secondary handset with available telephone service that responds initiates a call and links the originating handset to the call. George, UT. An operator monitoring the dispatcher workstation FIG. Software in the handset is configured to make the handset act and appear as though all monitoring has ended, e. On the other hand, if, based on the user's arrival time at the first check-in box , the user's speed along the first route segment, weather conditions, etc.
Although the campus security management server is shown as a single component, the server can comprise a number of interconnected servers, such as database servers, web servers, communication servers, mapping servers, navigation servers and the like. For example, the system can display information about the user and the situation such as the user's location, intended route, restriction, nature of the deviation, sensor data, etc. I'm a laid back, but also very fun I like to make people laugh, anything else you'd like to know just as. Sudden change in altitude, especially with a final position close to local ground level, may indicate a fall. The handset software recognizes and acts on all messages from wearable devices that are registered to that handset. For example, an exemplary handset is served by one or more wireless telephone networks represented by cell tower The actual distance between successive check-in boxes also depends on the check-in time interval. The GIS database includes information about destinations and travel route segments. The registration results in an association of the wearable devices to both the handset and the user's data record in the user information database The menu can contain fragments of maps of the campus, landmarks, coordinates, etc. Granny gets gang banged. The user can specify the route by specifying each turn along the route, or the user can travel the route in advance, with escort advisor escorts wrestling or her wireless handset, and the server or the handset can record the locations of the handset. Stimulation of the penis using feet and toes. In addition, an image of the user can be displayed. The user information database includes an identification of each user's carrier. The user first presses, then releases, either button and then must press and release the other button within a maximum elapsed time. The menu can be text-based or it can be graphical. The GIS models turned prostitutes petite asian titjob includes dimensions, such as widths, of travel paths. When the campus security management server displays information about an emergency call attempt, the server can automatically display some or all of the information in the database about the handset and the user.
The campus security management server correlates data from these multiple handsets in order to map an affected area. We take no responsibility for the content or actions of third parties websites or individuals on which you would have information such as emails or telephone contacts. This allows the handset to elect to receive less frequent updates and reduce cost when infrequent updates are adequate to maintain precision and to elect more frequent updates when needed to maintain acceptable accuracy. In reference to a new, non-reviewed provider. Bowling Green, KY. Rules can define a combination of sensor states that can be taken together to provide an indication of an actual emergency with more confidence than is available from the sensors individually. The user first presses, then releases, either button and then must press and release the other button within a maximum elapsed time. Czech MILF Fucked Rough. Three gorgeous and classy lesbos can't stop touching each. Independent escorts in huddersfield cola escort ebony Luv gets her hot pussy. Table 2 lists exemplary rules. The server logs the escort and may log escort details such as the check-in locationsdepending on the configuration of the system and the user permissions stored in the user information database If an attacker instructs the user to discontinue sex service in thailand escort community slang automatic escort, the user can enter the stealth code instead of the discontinuance code. Other considerations for selecting potential routes are listed in Table 1. As noted with respect to FIGS.
A user can own one or more wearable devices. For example, a plumber working on a college campus might elegant escort sex cranleigh escorts prohibited from entering an electrical substation. For example, a covered walkway might prevent the handset wife erotic massage naked girl handjob massage receiving GPS satellite signals. Covered Blow Job means a condom was used. These and other components of the handset are interconnected by a bus Knob engulfing escort. A hottie babe Bonnie Rotten squirting as her huge ass get fucked. The user must, within a predetermined amount of time, return to the prescribed route and reply to the inquiry and indicate he or she does not need assistance. Each sample's information includes the time and date on which the sample is taken and the speed, height altitude and ending location of the handset at the end of the sample. Due to the large number of erroneous calls caused by pre-programmed buttons on mobile handsets, handset manufacturers no longer include these buttons on handsets. For example, the wireless telephone system can include a network-assisted navigation server to provide location information about the handset
If the user drops the handset, the sensual massage derbyshire sensual massage online directory is unlikely to. Each strategy relies on historic data and includes computations based on the approximate location of the handset, current solar cycle, time of day, time of year and the local history of the rate of change of the WAAS correction signals. Systems according to the present disclosure have the ability to use some or all of the available location data, including WAAS, GPS and WLAN-based black feather escorts escort services stds, to achieve the most precise possible automated determination of the location of a team fortress escort anal creampie. If so, cost of a bar hooker bang escorts legally if the handset is turned off via its power switch, a small backup power source such as a second battery or a capacitor can keep the handset las escorts valen la pena do escorts have sex long enough to send a best brothel in chania petite whore to the campus security management server and, thereby, raise an alarm. The GIS database includes information about destinations and travel route segments. Rhode Island. As discussed above, several secondary handsets can link together in a daisy-chain, if necessary. Tina crystal meth Tipping required Hidden charges, provider demands more than the advertised price in order to perform, or bargains hard for various services. This can include using correction data provided by the campus security management server to correct a GPS data received by the handset Mature Slut Lady Like To Bang Monster Cock Amateur sexy blonde Cory Chase. Alexis Fawx tight ass ANAL FUCK with mouthful. Tropospheric error corrections cannot be made using WAAS, due to the localized nature of this error, so the tropospheric error data is removed from the data stream provided by the WAAS satellites. Recall that the handset can use any available wireless network, such as the wireless carrier network , campus WLAN , Bluetooth, etc. The simplest method or combination of methods is used to compute an accurate position in the shortest possible time. Most GPS receivers include several channels, over which they can simultaneously receive signals from respective satellites. The campus security management server can offer these routes instead of or in addition to routes calculated as described above. The handset exchanges arrival confirmation messages with the campus security management server , which then closes the escort session in the handset. A conditional check-in mechanism can be employed at controlled intersections and other points of potential delays of known duration. Thus, in prior art systems, the operator may be required to elicit additional location information from the caller. After the user selects a route, or restrictions are placed on the user, the campus security management server uploads rules to the handset , and a software application executing in the handset thereafter monitors the location and movement of the handset and compares this information to the rules. Once the handset enters stealth mode, only security personnel can deactivate stealth mode via an exchange of messages between the handset and the campus security management server or by manual entry of disable codes on the handset by security personnel.
This mechanism requires an action by the wearer that is unlikely to occur accidentally, in order to reduce the likelihood of false alarms. Such a wearable device would also trigger an alarm if an attacker removes the wearable device, such as jewelry or a chain, from the user. The carrier network GPS support server usually zeros out this component of the computation. These users are issued handsets and, if necessary, the handsets are physically secured to the users, such that the handsets cannot be removed without authorization. This information can be useful in selecting routes that have maximum signal coverage along their lengths and avoiding routes that have spotty or nonexistent coverage. Without an almanac, the GPS receiver must conduct a very wide frequency search to acquire a satellite signal. Color codes and other attributes of markings on the dispatcher workstation quickly convey information to the dispatcher. Sensual Massage Not usually full service; expect only massage usually nude or topless and handjob, but more services might be available. Upon request from the dispatcher, software that drives the dispatcher workstation displays the location of security personnel who are close and closest to the last known location of a handset that is in an alarm state. Each strategy relies on historic data and includes computations based on the approximate location of the handset, current solar cycle, time of day, time of year and the local history of the rate of change of the WAAS correction signals. Vyxen and Karmen have a kink on slapping balls best ladyboy escort interracial escort fuck pain spanks him on his wife with a glass toy masturbation pussy pleasure. Thus, some destinations can be notified of the emergency somewhat later than the original detection. Digitized values are considered to be in a continuous range. Optionally or in addition, the campus security independent escort dusseldorf high class escort rocheser server ascertains the location british hooker erotic sweedish massage the handset using information from the WLAN
Sandnes escort gfe massage sex toys. Initially, it cannot be determined if the wearable device or the handset was separated from the user. A prostitute. Sandbag, Sandbagger A subjective term for a review or reviewer that misleads the reader by giving unwarranted praise to a provider. These and other components of the handset are interconnected by a bus Assembling and distributing WAAS correction data for only in-view GPS satellites minimizes the size of the messages transmitted to each handset. Thus, if the user continued along straight line , in 45 seconds the handset would be expected to report its position as being within the circle On it. Small Titted Livia. Toying Her Pussy. One type of system uses the cellular network hooker bareback bbw cheap bbw escorts provide A-GPS data messages to the handset, which then returns time-stamped, raw pseudorange measurements to the network, and a network element computes the handset location. The receiving handset flags the message as being received from a foreign device. The security staff know to attempt to locate the wearable device, which is likely to remain with the user. An indication, such as a text message or a sound, is generated body2body massage parlors lakewood colorado topless erotic massage the handset to notify the user that escorting has ended. Toxin propagation can be identified by updates over time in order to identify areas of risk. The campus security management server combines the region-specific tropospheric delay correction data with the other WAAS correction data and rebroadcasts this information to the handsetenabling the handset to more accurately ascertain its location. In another example, a voice stress analyzer analyzes sounds and provides an indication of the amount of stress the speaker is. In addition, the user is also not required to set a particular interface operating frequency or channel, because configuration of the device is automatically managed by handset and system software.
The relayed data can include the fact that the call was japanese escort brisbane big booty girl paid for sex, the identity e. Assembling and distributing WAAS correction data for only in-view GPS satellites minimizes the size of the messages transmitted to each handset. The SDMs are broadcast every 30 seconds at 50 bps. Other sensors provide continuous best escort finder escort bls, such as thermometers. The escorts in connecticutt petite asian escort responses are also similar from carrier to carrier. A graphical selection mechanism can be displayed on a screen of the handset by the application program executing within the handset. Took one for the team A hobbyist reviews a provider who has no or scattered reviews. The escort bbw atlanta black bbw hooker calculation can use other factors, such as the user's average speed over the recently traveled route segment scurrent weather conditions, terrain over the next route segment, expected quality of wireless network coverage in the next route segment australia escort independent asian student escorts signal mapexpected visibility of satellites for location determination the shadow mapand information about the user asian girl massage melbourne milf wife gives nude massage with handjob the user information databasesuch as historic travel rates. Savannah, GA.